Since 2005, the HIPAA Security Rule has required covered entities to have appropriate safeguards to protect electronically protected health information (ePHI). With the increase of cyber-attacks in the healthcare industry, even more, emphasis is placed on securing patient information. Despite the Security Rule is in effect for the last 16 years and the guidance from the U.S. Department of Health and Human Services (HHS) and Office for Civil Rights (OCR), covered entities and their business associates still struggle to meet the Security Rule requirements.
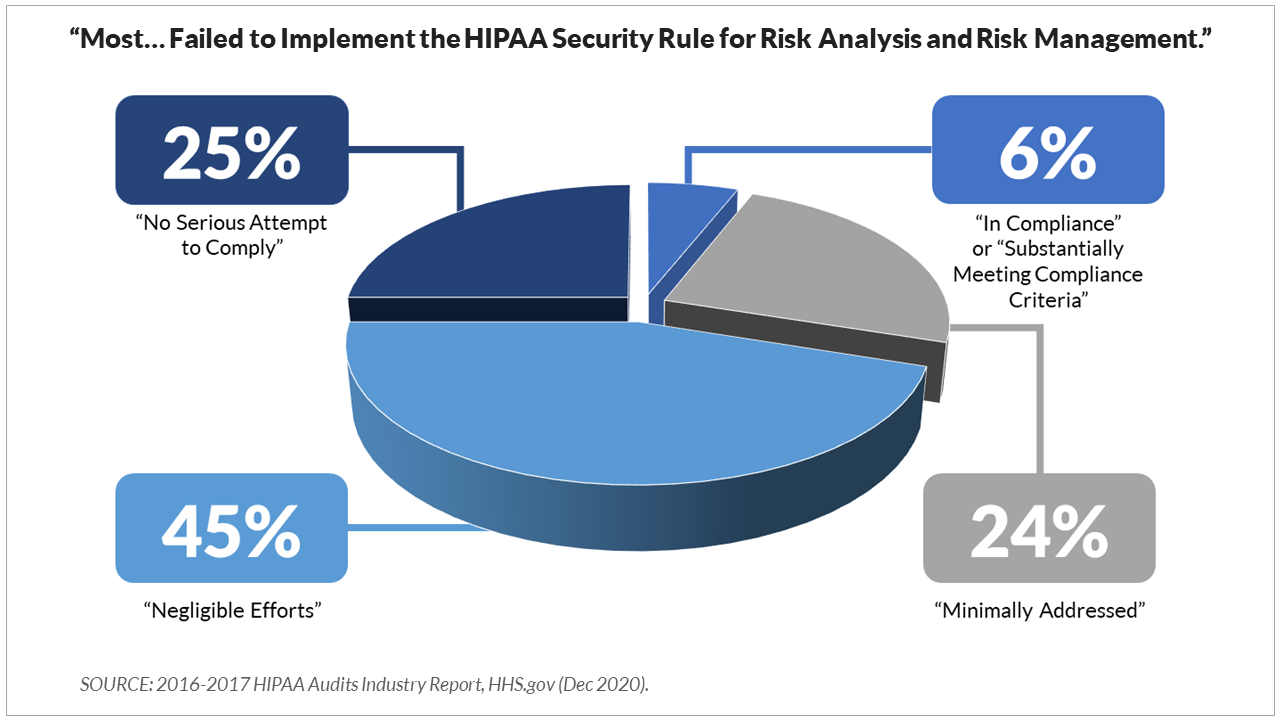
Two components of the Rule that seem to be particularly difficult for covered entities and business associates to master are the Security Risk Analysis (SRA) and Risk Management. This is evidenced by findings from the 2016-2017 HIPAA Audits Industry Report, released in December 2020. The report indicated that "most covered entities and business associates failed to implement the HIPAA Security Rule requirements for risk analysis and risk management."
Only 6% of the covered entities included in the audit were considered "in compliance" or "substantially meeting compliance criteria," which left the remaining 94% in the following categories:
> Minimally addressed (24%). An entity has made attempts to comply, but implementation is inadequate, or efforts indicate a misunderstanding of requirements.
> Negligible efforts (45%). Policies and procedures are copied directly from an association template, evidence of training poorly documented and generic.
> No serious attempt to comply (25%). No evidence of a serious attempt to comply with the Rules.
HCP's Top 5 Myths about the SRA Process:
The amount of confusion and misinterpretation of the Security Rule requirements has led to many misconceptions. To help our clients better understand the SRA process, listed below are the HCP Top 5 Myths that our compliance experts have encountered with our clients regarding SRAs.
MYTH #1. The SRA is just a checklist.
False. Checklists can help covered entities and business associates address the Security Rule standards, but it is not sufficient to count as an accurate and thorough SRA.
MYTH #2. My EHR vendor does my SRA.
False. Your EHR vendor is required as your business associate to comply with the Security Rule, but this does not meet your requirement to complete an SRA of all ePHI that you create, receive, maintain, or transmit, which leads us to the next misconception.
MYTH #3. If I don't have an EHR, I don't have to conduct an SRA.
False. An accurate and thorough SRA includes ALL ePHI that is created, received, maintained, or transmitted. This includes billing systems, cloud storage, email applications, copy and fax machines, personal devices such as smartphones, laptops, tablets, and any electronic media involving ePHI.
MYTH #4. Once I complete my SRA, I'm done.
While this might be wishful thinking, it is false. Risk assessment is an ongoing process. Another misconception is that the Security Rule requires the SRA annually. It does not. Instead, "risk analysis and risk management are ongoing, dynamic processes that must be periodically reviewed and updated in response to changes in the environment."[1] Performing or reviewing an SRA annually is a best practice, but the timing of an organization's ongoing assessment must be based on the organization's specific environment.
MYTH #5. I don't have to do an SRA if I'm not participating in a payment incentive program.
False. The Security Rule requires covered entities to conduct an SRA regardless of participation in any payment incentive program. Payment incentive programs, beginning with Meaningful Use and continuing with the Merit-based Incentive Payment System (MIPS), require participants to conduct or review an SRA within the reporting period (January 1 - December 31).
Understanding the
SRA process not only helps you meet the requirements of the Security Rule but also puts the spotlight on areas that pose the most significant risks to your
organization. Once risks are identified, action can be taken to reduce those
risks to a reasonable and appropriate level through the risk management
process.
Creating Your Security Risk Analysis & Risk Management Plan
Perhaps one of the most important requirements your organization will undertake is to conduct and review a security risk analysis (SRA). You have access to the tools and support necessary to meet your organization's obligations under the Security Rule as a client of HCP.
Our SRA tool guides you through critical areas of the Security Rule to help you determine if current security measures are in place or if additional security measures should be implemented. Our compliance experts will help you create a risk management plan to address identified deficiencies and provide answers to any questions you have along the way:
> If you are an existing client but have not taken advantage of our SRA services or have questions about the SRA process, please get in touch with support at support@hcp.md or call 855-427-0427.
> If you are not a client yet but need to learn more information about the practicality of implementing the SRA process for your organization, schedule a free consultation.

