Cyberattacks are Rising in Healthcare
Patient data is such an increasingly valuable commodity on the black market that cybercriminals seek to gain unauthorized access to protected health information (PHI) by any means.
Hacking Emerges as the Top Threat to PHI
The Office of Civil Rights (OCR) published its Oct 2022 Cybersecurity Newsletter showing an increase in cyberattacks by 42% for the first half of 2022 alone. In addition, cyberattacks targeting the healthcare industry increased by 69%.
The numbers are trending higher with the rise of data breaches occurring in the healthcare industry. Breaches that affected 500 or more individuals' unsecured Protected Health Information (PHI), including Electronic Protected Health Information (ePHI), reported to the OCR, increased from 663 in 2020 to 714 in 2021.
Of the
breaches reported to the OCR in 2021, 74% involved hacking or Information
Technology (IT) incidents alone. Hacking is now the greatest threat to the
privacy and security of PHI in healthcare. A timely response is the best way to
prevent, mitigate, and recover from a cyberattack.
Recommendations for a Security Information Response
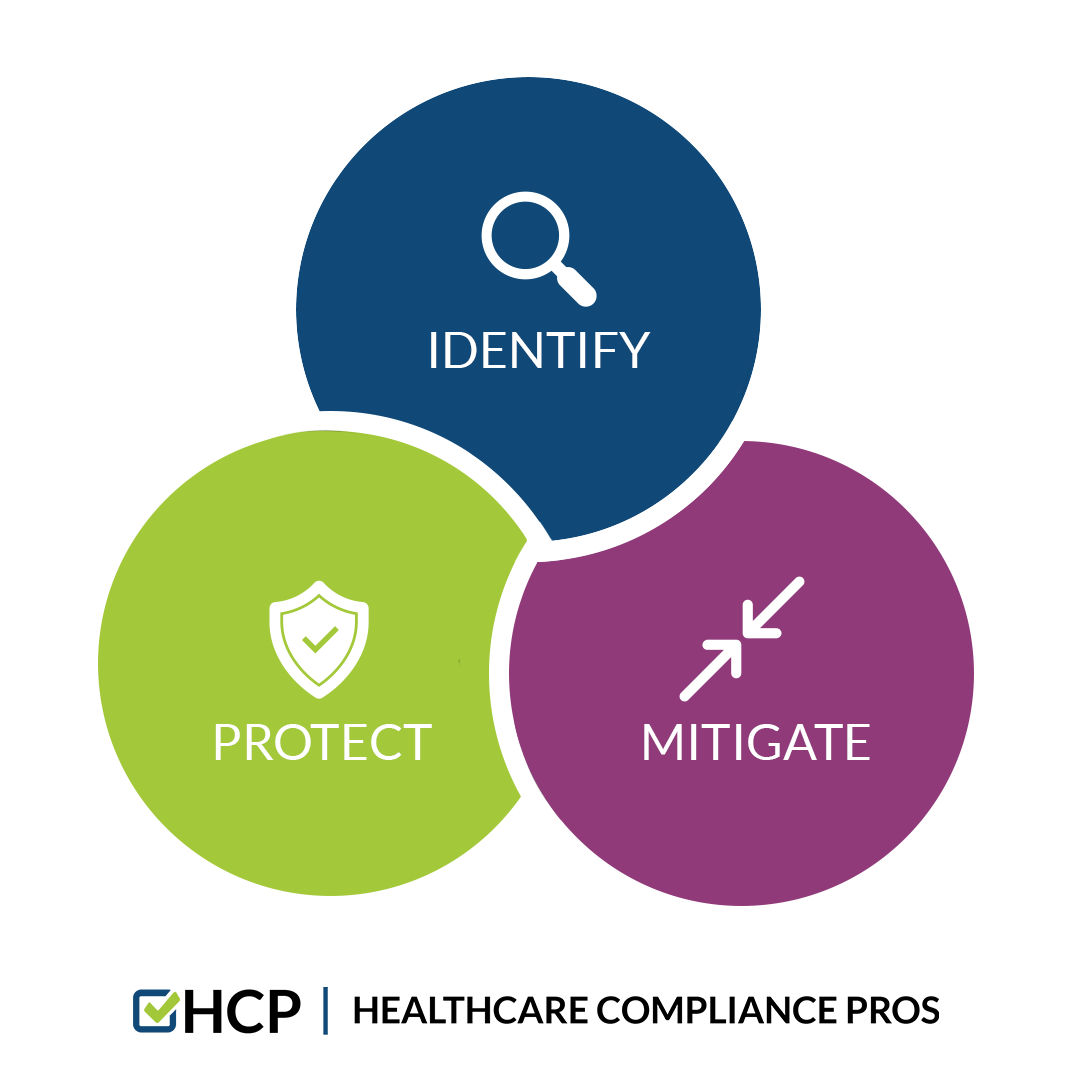
Creating and
implementing a Security Information Breach Notification Policy is a top
recommendation from Healthcare Compliance Pros (HCP).
Identify the Risks
Your policy should define
the minimum requirements and your responsibilities for reporting security
incidents to minimize the negative impact on the confidentiality, integrity,
and availability of your company's resources and information systems.
You will want to ensure that your staff is educated on identifying security incidents and the proper response steps. The ability to identify a threat quickly enables you to mitigate the issue and respond appropriately.
Mitigate the Risks
Another way
to help you ensure the safety of your ePHI is by maintaining a detailed Asset
Inventory. This will help you to locate which devices may be affected. This
list should also track software and data assets which you can use to determine
what applications will need to be brought online and in which order. HCP offers
a detailed Asset Inventory Log that you can utilize to assist you with this
process.
Next, you will want to know how to report a breach properly. HCP offers a HIPAA Incident Log, where you can report all potential breaches. Once your incident is submitted, your Compliance Consultant will get right to work. Based on our comprehensive review of your incident, you will be provided with the necessary mitigation steps. If it is determined that a breach has occurred, a report to the OCR is a must. However, don't forget to follow your state laws, as these can be more stringent in some cases.
Protect Your Organization
A final
reminder when it comes to HIPAA requirements is your organization must have a
documented policy in place (it's not a should, it's a must). In the eyes of HIPAA regulators,
it does not exist if it is not documented. For more
information and assistance with creating documentation, please reach out to
your support team about navigating all things compliance.
Final Thoughts to Achieve HIPAA Compliance
Safeguarding the privacy and security of patient data must be a top priority for healthcare clinics, providers, and facilities. Covered entities and business associates must generate policies and procedures that maintain the confidentiality, integrity, and availability of ePHI.
Supplemental Compliance Resources:
- HHS "Health Industry Cybersecurity Resources
and Templates: Managing Threats and
Protecting Patients" (View PDF
https://405d.hhs.gov/Documents/resources-templates-508.pdf)
- Ready.Gov "IT
Disaster Recovery Planning" (Explore Page https://www.ready.gov/it-disaster-recovery-plan)
- NIST "Computer Security Incident Handling Guide" (View PDF https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf)
- NIST "Guide
to Integrating Forensic Techniques into Incident Response" (Learn More https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=50875)
- NSA "Top
Ten Cybersecurity Mitigation Strategies" (View PDF https://www.nsa.gov/Portals/70/documents/what-we-do/cybersecurity/professional-resources/csi-nsas-top10-cybersecurity-mitigation-strategies.pdf)
- OCR "Cyber Attack Quick Response Checklist" (View PDF https://www.hhs.gov/sites/default/files/cyber-attack-checklist-06-2017.pdf)
Not an HCP client yet?
Discover how to implement a customized security incident response plan for your organization by scheduling a free online consultation.