Cybersecurity Vulnerabilities - How to Lower Your Organization's Risk
JUMP TO THE SECTION
- The Emerging Cyberworld for Healthcare
- Cybersecurity Vulnerabilities
- Ransomware Response Checklist
- What About Social Media Concerns?
- What Must Healthcare Organizations Do to Protect Themselves?
- Identify a Social Media Policy & Procedure
- Mitigate Risks with Cyber Liability Insurance
- Implement the Right Protection
The Emerging Healthcare Cyberworld
Organizations and people everywhere need to know how to navigate the cyber world safely and effectively. Increasingly, the boundary between what is in real life (IRL) and what is part of the cyber world is becoming less clear.

Our cyber world was already growing rapidly before COVID-19 and then, after the pandemic hit, its growth accelerated even more so. Now, more organizations run their businesses dependent on technology (i.e., email, virtual meetings, and social media). The use of these technologies helps maintain contact with customers, family, and friends.
For healthcare organizations, the benefits from the cyber world include visiting more patients through telehealth appointments, providing more access to patient records with patient portals, and contacting patients via email. These cyberworld advancements offer easier and faster solutions in most of our lives (IRL). However, simultaneously, we've opened up and exposed vulnerabilities that malicious actors will seek out for their advantage.
Cybersecurity Vulnerabilities
To protect against your cybersecurity vulnerabilities, organizations need to identify threats and understand their risk to attacks such as ransomware or phishing scams. According to the Cybersecurity & Infrastructure Security Agency (CISA), ransomware is an ever-evolving form of malware designed to encrypt files on a device and remove access to as many files as possible while corrupting the systems that rely on them to become unusable. If you want your files or systems back, then wait for the malicious actors to demand a ransom in exchange for decryption. Furthermore, ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid.
In recent years, ransomware is increasingly prevalent as malicious actors continue to grow in number and evolve their attacks with more insidious methods. A recent report by SonicWall logged nearly 500 million ransomware attacks through September 2021. (!!) The odds of experiencing a ransomware attack is surging and, consequently, increasing the collective risk towards the healthcare industry. Your organization must face how to respond in the event of a ransomware attack to succeed.
Ransomware Response Checklist
While there are several methods for responding to a cyberattack, Healthcare Compliance Pros recommends following the Cybersecurity Advisory Committee (CISA) guidance when responding to a ransomware attack. The ransomware guide is a published checklist provided by a joint initiative from CISA and the Multi-State Information Sharing and Analysis Center (MS-ISAC CISA). The carefully gathered information serves to guide organizations throughout the response process (from threat detection to containment, and then eradication).
View the Ransomware Guide consisting of two parts:
Part 1: Ransomware Prevention Best Practices
Part 2: Ransomware Response Checklist
Every industry and organization must defend its networks,
systems, and users against cybersecurity threats, especially when you consider
the statistics.
2021
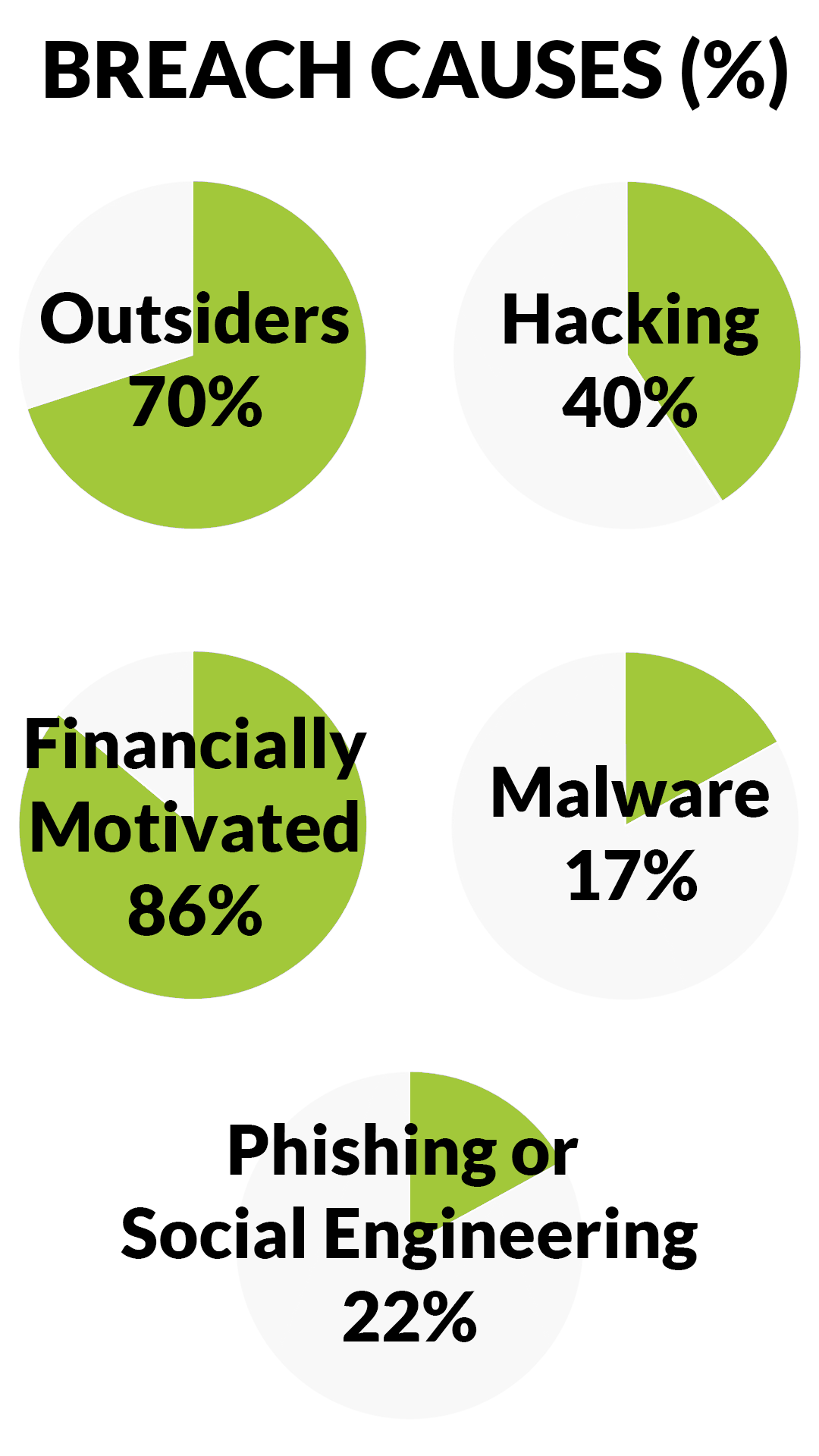
Verizon's Data Breach Investigations Report (DBIR) identified these overlapping
causes:
- 70% of breaches were caused by outsiders.
- 45% involved hacking.
- 86% were financially motivated.
- 17% involved some form of malware.
- 22% featured phishing or social engineering.
The
International Data Corporation (IDC) predicts that 55.7 billion connected
devices will be connected by 2025, of which 75% will be connected to the IoT (Internet
of Things).
Furthermore, IDC estimates that IoT devices will generate
73.1 zettabytes of data by 2025 (up from just 18.3 zettabytes in 2019).
"Tweet," "Snap," "Like," or "Follow Me"! Regardless of
someone's desire to own a personal account, social media operates with users
everywhere and exists as a business process. Any business with an internet
connection can leverage social media as a beneficial marketing tool: a great
way to disperse information, find new customers/patients and increase
demand/popularity.
However, the harmful effects of social media are becoming evident too. Examples of harm to organizations due to poorly thought out social media usage might include:
- Security risks from phishing scams, hackers, human error, etc.
- Inadvertently sharing Protected Health Information
- Damage to the organization's reputation
- Inability to manage comments
- Brand hijacking and spam
Building trust appears to take a lifetime to build and
seconds to destroy. When organizations are choosing social media practices to
engage with people online, HCP recommends providing proper-use training to your
staff members. If your organization must have a social media account, we
recommend social media management training to ensure your organization's
accounts are properly maintained.
Pay extra attention to your interactions on social media,
because healthcare organizations must remain HIPAA-compliant at all times
online. For more information and guidance, please refer to our article, Posting
with Caution: Social Media and HIPAA Compliance.
What Must Healthcare Organizations Do to Protect Themselves?

According to the U.S. Department of
Health and Human Services (HHS), an organization's use of social media must
follow all current laws and standards related to HIPAA and any other applicable
information technology law and standards. Healthcare organizations should have
a documented, implemented, and enforceable social
media policy that includes the following procedures:
- Maintaining compliance standards for patient privacy and confidentiality.
- Setting a requirement for employees to separate their personal and professional social media accounts.
- Enforcing all necessary privacy settings are a requirement to open personal and professional social networking websites.
- Observing procedures for all ethical boundaries and guidelines while connecting with patients through the employee's professional social media account(s).
- Addressing how to respond to unfavorable comments on healthcare rating websites and advising employees about other critical response procedures.
- Instructing staff to never post or share anything defamatory, profane, libelous, threatening, harassing, abusive, obscene, knowingly false, or otherwise inappropriate.
Mitigate Risks with Cyber Liability Insurance
Cyber liability insurance is designed for organizations as
an insurance policy with protective coverage against events like data breaches
or other cyber security issues.
An excellent cyber liability insurance policy will require immediate notification as soon as an
organization becomes aware or detects a possible breach following a cyber-attack,
such as ransomware. Hypothetically, your organization won't
make a successful claim through the cyber liability policy unless you contact your
insurance company as soon as a possible breach occurs. Ensure that you have
the provider's full guidance and steps to receive maximum benefits.
If your organization does not have cyber insurance coverage yet, HCP highly recommends discussing a policy with your insurance agent right away. Cyber insurance is a critical part of a secure IT environment within the healthcare industry due to the imminent threat of cyber-attacks from bad actors.
Implement the Right Protection
Overall, setting the right policies and procedures in place will go a long way to organizing your efforts later. Although you can spend hours with DIY research about how you can protect your organization in the cyber world, we recommend finding and implementing the appropriate precautions towards the right protection.
Save time: Access our Compliance Resources
We found it for you so you wouldn't have to. Ask one of our dedicated advisors how you can best protect your organization with:
- Customizing a Sample Social Media Policy tailored to your needs
- Learning the best practices and procedures that mitigate cyber risks
- Educating your employees with our Cyber Security Training Courses
Got Questions?
For more information or if you require additional
assistance, contact our dedicated support team by email support@hcp.md or call 855-427-0427 or online.
Not an HCP client yet?
The easiest way to learn how to solve
your compliance is to schedule a free online consultation.

