- Are you aware if a HIPAA incident happened within your organization?
- Do you know if this incident was reportable or not reportable?
- Have you taken the proper notification steps for individuals?
- What about the proper notification steps for the OCR?
- Are you logging documentation throughout the year?
- If not a reportable incident, do you know if the disclosure log properly documents the incident?
When a health practitioner experiences a data breach, protected health information (PHI) can be exposed, and the ramifications will be noticed. However, the damage caused by insider threats and outsider threats can be severely restricted. Although outside threats from malware and hackers are sensational, the reality is often due to common insider threats ranging from lost or stolen PHI devices or employees making honest mistakes that result in PHI breaches.

PHI Data Breaches are a matter of "when" for the health industry, as seen in the frequently updated OCR Breach Portal. Damage limitation is the primary goal for health professionals. Continuous preparation and corrective actions are crucial for covered entities and business associates. Do you know your organization's response plan for health data breaches?
The Breach Notification Rule is an important aspect of an effective HIPAA Compliance Program, making up approximately 15% of the total requirements. Neglecting any aspect of HIPAA regulations is not an option for success, so avoiding financial penalties requires a healthy respect for the Breach Notification Rule.
"The HIPAA Breach Notification Rule, 45 CFR §§ 164.400-414, requires HIPAA covered entities and their business associates to provide notification following a breach of unsecured protected health information." (HHS.gov).
Lions, Tigers, and Bears. OCR!
The Office for Civil Rights (OCR) has initiated over 1,154 compliance reviews and received over 319,816 HIPAA complaints in total. In 97% of these situations, a resolution was reached by the OCR, and the agency was able to enforce the HIPAA Rules by securing corrective actions in every situation where an inquiry revealed a violation. Overall, the OCR has reached settlements or assessed civil monetary penalties totaling over $134,828,772.00.
Check out the "Top 5 HIPAA Compliance Issues to Address in 2023" based on the OCR Enforcement Results as of January 31, 2023.
Furthermore, a recent study by Verizon reveals that healthcare is the only industry in which insiders are the biggest threat to data security (i.e., insider threats accounted for 59% of all reported security incidents). The evidence demonstrates the need for healthcare entities to implement comprehensive security measures, respond to breaches promptly, and safeguard patients' PHI.
What is Your Health Data Breach Response Plan?
HIPAA Compliance Question: Did your organization experience a breach incident last year? The OCR mandates March 1st as the annual reporting deadline for the HIPAA covered entities and business associates that experienced any breaches affecting fewer than 500 individuals.
Identify. Mitigate. Protect. Helping you to solve compliance is our team's highest goal, so HCP follows a process of due diligence that protects your organization from unnecessary HIPAA fines and penalties. Here is a quick outline of our HIPAA recommendations and questions summarizing an effective breach incident response plan.
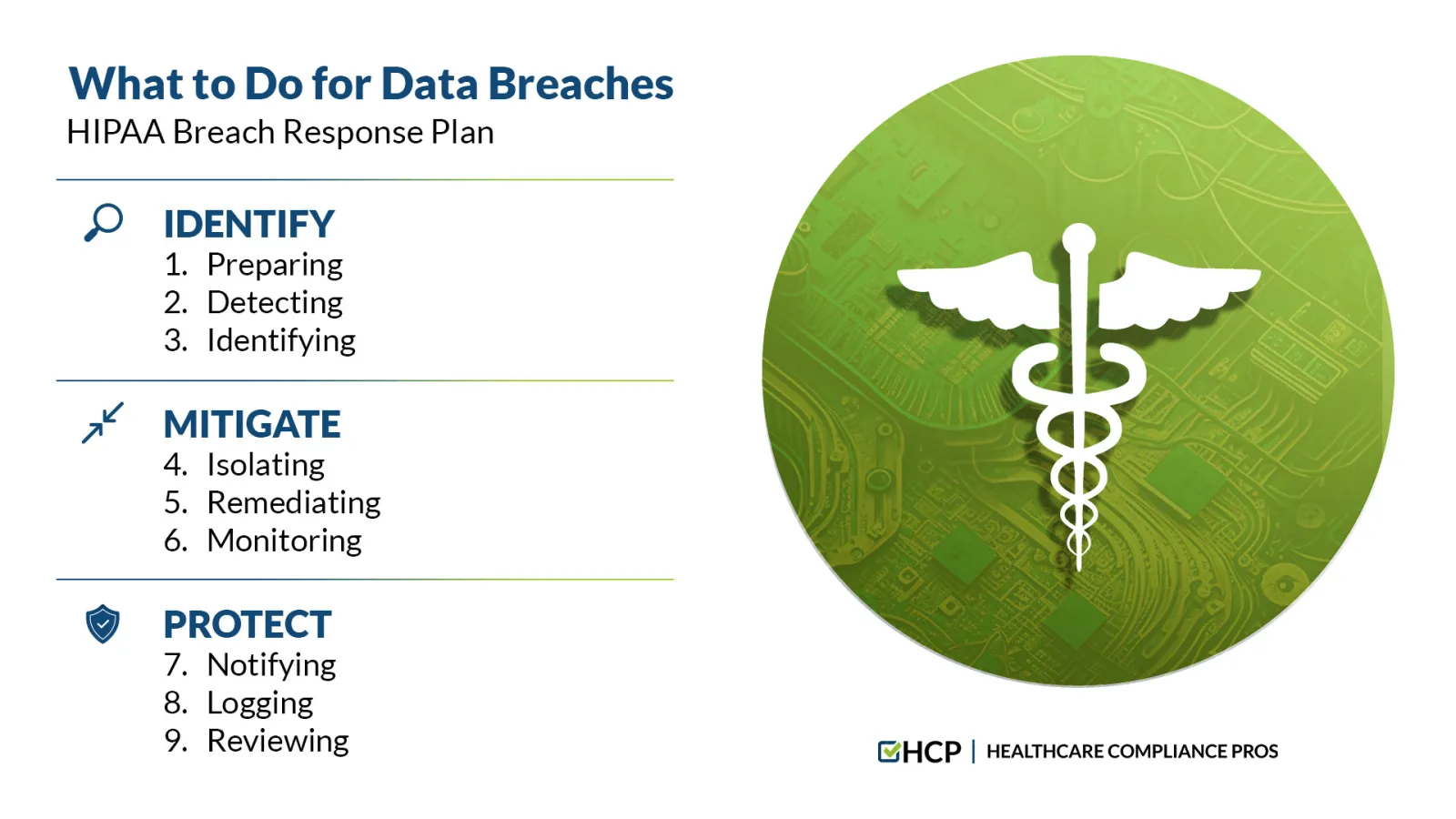
IDENTIFY:
1. Preparing — Learn from past breaches and prepare for future breaches.
Most breaches are the result of insider threats, which can be caused by human error. Preventing cyberattacks is crucial, but addressing reality often deals with common PHI breaches due to personal cars getting broken into, laptops being physically stolen, perhaps faxes being sent to the wrong fax number, or emails delivered to the wrong recipient, and so on.
- Are you addressing breaches caused by human error?
- Do all workers know their duties and responsibilities to prevent insider threats?
- Do you regularly test your reaction plan?
2. Detecting — Contain and assess the breach as early as possible.
Detecting a security data breach early reduces damage. Perhaps theft of an employee's device caused the incident, or your network may have malware installed. Regularly scanning networks for vulnerabilities is essential. In cases when enforcement agencies need to be immediately alerted, their input may affect your breach response.
- How do you know when a breach occurs?
- Can you implement the breach response plan immediately?
- Have you alerted relevant law enforcement agencies (if necessary)?
3. Identifying — Quickly determine the breach's cause and scope.
Discover the source as quickly as possible and understand the negative influence to cut off unauthorized access. Identify the source of the breach and brainstorm options to limit unauthorized access. Know your opponent to reduce and eliminate the threat.
- Who is the culprit or the cause?
- What is the threat severity level?
- What caused the breach incident?
MITIGATE:
4. Isolating — Isolate the insider threats through the investigative process.
A system may be compromised in more than one place. For the severe cases like stopping a cyberattack, turn off all vulnerable systems. Stop data access and PHI exfiltration immediately. Examine all systems/equipment to see if other network regions are impacted.
- Are all cybersecurity vulnerabilities being address to lower your organization's risk?
- How can you prevent data access and PHI exfiltration?
- Have you examined all systems/equipment to check for other network regions that may be impacted?
5. Remediating — Eradicate the harmful elements and neutralize the cause of the breach.

Safeguarding data is crucial. Remediation options might include removing malware, patching vulnerabilities, canceling user access, improving employee training and awareness, etc. Data exfiltration may be prevented even once access is achieved. Before removing access/infections from critical systems, backup data regularly and completely.
- What measures can be taken to eradicate the breach cause?
- How can you prevent data exfiltration?
- Do you have a regular and complete backup of data before removing access/infections from critical systems?
6. Monitoring — Check affected systems for abnormalities and monitor compliance safeguards.
To determine data exposure and assault severity, forensic data analysis should be performed. A process of due diligence to address human errors can go a long way to safeguard your data and your organization. Consult data security professionals and conduct a security risk assessment to detect new security vulnerabilities.
- Are you conducting a regular security risk assessment to protect yourself and your organization?
- Are you checking affected systems for abnormalities and remediating compliance?
- Are you consulting compliance advisors to conduct a risk assessment to address security vulnerabilities?
PROTECT:
7. Notifying — Notify the pertinent government agencies and impacted stakeholders when necessary.
You have up to 60 days to issue breach notification letters to victims and to report the security breach to the OCR but in reality you are obligated to respond immediately to the incident. When more than 500 individuals are affected, the covered entity must also notify HHS and, in some cases, the media. Prompt notification can lessen the effects of a data breach, so be sure to consider the timescale requirements that vary state by state.
- Do you know whether the breach incident is reportable or an exception?
- Are you aware of the timescale requirements for notification that vary state by state?
- Can you confirm the pertinent government agencies and impacted stakeholders were notified?
8. Logging — Log all HIPAA breaches regardless of if they are reportable or considered an exception.
HCP's recommended best practice is to log all incidences and help your organization identify areas that require greater workforce training or retraining. Incidents should be discussed with all staff as a compliance training exercise and additional HIPAA training should be offered to the employee(s) responsible.
- Are you logging all HIPAA breaches regardless of if they are reportable or consider an exception?
- Are you discussing incidents with all staff as a compliance training exercise?
- Are you offering additional HIPAA training to the employee(s) responsible?
9. Reviewing — Test incident management methods and procedures to improve security.
Any data security gaps must be closed. After a PHI breach, regulators expect security weaknesses to be fixed quickly. Failure to address security concerns will result in HIPAA fines, not just data breaches. To prevent future breaches, HCP advises consistently review the effectiveness of policies and processes.
- Are you reviewing and testing incident management methods and procedures to detect holes and improve security?
- Are you closing any data security gaps?
- Are you reviewing policies and processes to prevent future breaches?
Rinse and repeat — Responding to breach incidents must be considered a cycle of corrective actions. Fostering an atmosphere of compliance will require these nine repeatable steps.

Final Thoughts & Access to HIPAA Compliance Resources
To help you understand and meet your organization's requirements throughout the year, HCP offers the following HIPAA Compliance resources:
- Breach Decision Tool — Analyze a potential breach of the HIPAA Privacy and Security Rule. Our form will assist you to understand what documentation is necessary and determine whether breach notification is required under HIPAA.
- Quick Reference Breach Checklist — Another helpful tool so you can handle reporting incidents.
- Log Breaches Faster — You can log breach incidents when they occur throughout the year using our online tool.
- Disclosure Log Tool — To identify which incidents are not reportable, you can easily document incidents for due diligence.
- Scalable LMS Workforce Training — To educate your employees on all things HIPAA, Cybersecurity, and more.
- Compliance Advisor Support — You can submit your breach report to a compliance advisor, review the breach determination, and enable mitigation services.
Are you already an HCP client? Ensure that you maximize your compliance features by logging into the HCP Portal. Contact your dedicated team of compliance advisors when you need assistance.
Not an HCP client yet? Schedule a free online consultation to learn about building an "audit proof" compliance program (HIPAA, OSHA, Corporate, Coding, and more).
Watch the Free HIPAA Webinar
View the educational HIPAA Webinar: "HIPAA Health Data Privacy & The Right of Access"
- Description: There
exists a high-stakes question, 'How to manage Protected Health Information
(PHI)?' Learn essential stories curated by our compliance experts who uphold
PHI requirements within effective HIPAA Compliance Programs nationwide.
- Watch On Demand (No Charge via Zoom).

This information is offered for educational purposes only, and you should not construe this information as legal advice. Specific legal questions regarding these topics should be addressed with one's own counsel.

