Protected Health Information: The Basics You Need to Know
Protected health information (PHI) is a term often heard in the healthcare industry in relation to HIPAA laws, but what does it mean exactly?
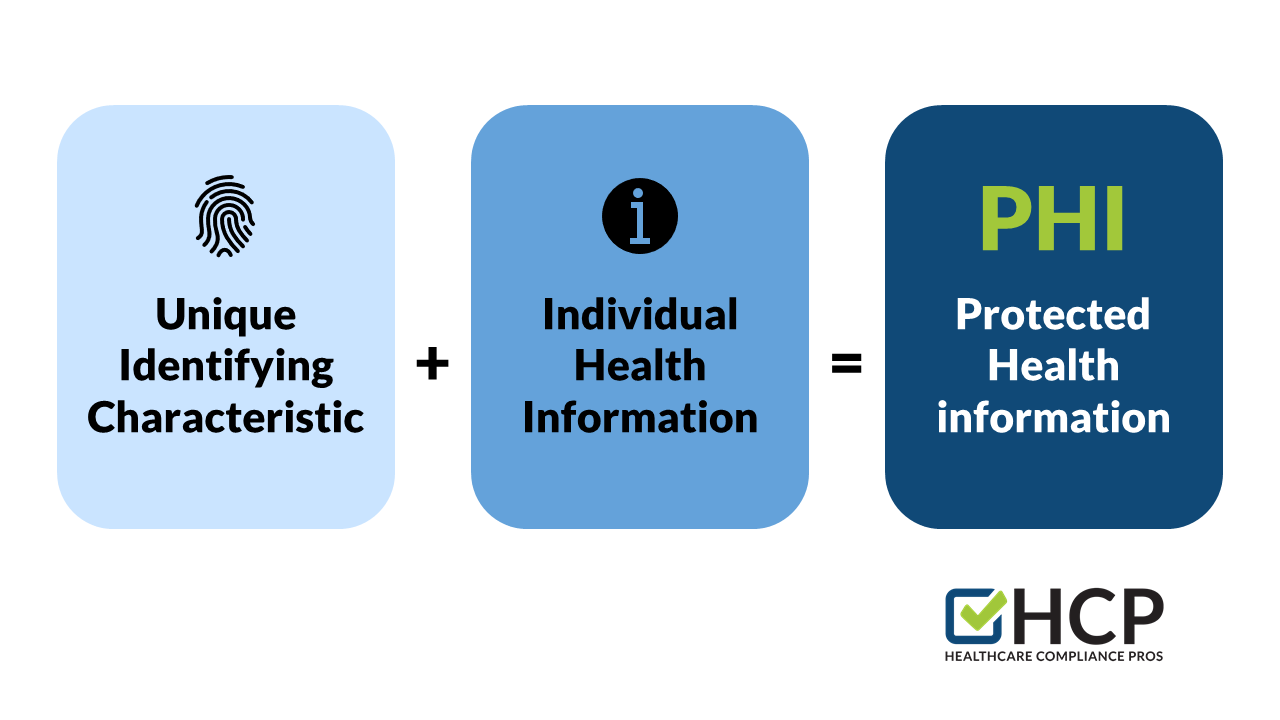
- PHI refers to specific information that can identify an individual or their health status.
- Electronic protected health information (ePHI) is another kind of protected health information (PHI) that is generated, saved, transferred, or received in a digital format.
- The Health Insurance Portability and Accountability Act (HIPAA) outlines the responsibilities that organizations have to protect PHI
Ensuring that PHI remains under protection is vital to staying in operation. Covered HIPAA entities are responsible for maintaining patient confidentiality to avoid revealing an individual's identity, medical history, or payment history. There are 18 different personal identifiers that, when included with patient health information, designate that information as "protected."
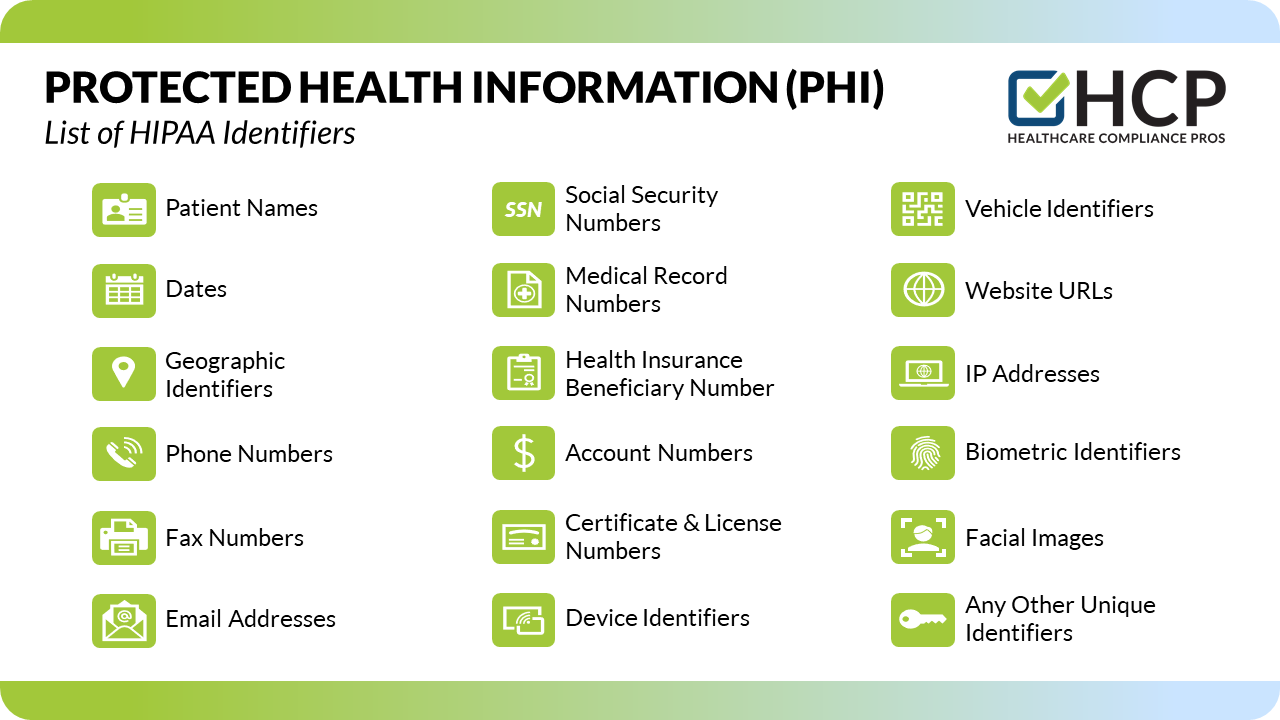
What is Covered as PHI?
The 18 Types of Personal Identifiers of Protected Health Information (PHI):
- Patient Names
- Mailing Addresses, Zip Codes, & Geographical identifiers
- Dates Related to Individual
- Phone Numbers
- Fax Numbers
- Email Addresses
- Social Security Numbers
- Medical Record Numbers
- Health Insurance Beneficiary Numbers
- Account Numbers
- Vehicle Identifiers & License Plate Numbers
- Certificate & License Numbers
- Device Identifiers & Serial Numbers
- Website URLs
- IP Addresses
- Biometric Identifiers, Fingerprints, Retinal, & Voiceprints
- Facial Images & Recognition
- Any Other Unique Identifying Characteristic

Why is PHI protected and what does that mean for you?
PHI is designated as "protected" in order to safeguard the privacy of individuals. Due to the required and addressable safeguards of HIPAA, patient information must be treated sensitively. These requirements mean that it is the responsibility of the employer to create policies and procedures in order to maintain the integrity of PHI, provide compliance training sessions, and make sure the policies and procedures are easily accessible to all employees. What reasonable and appropriate safeguards does your organization have in place in order to protect PHI?
Who is Covered by HIPAA?
HIPAA Covered Entities (CEs) under the Act, such as health plans, healthcare clearinghouses, and healthcare providers, are responsible for safeguarding PHI and ePHI. HIPAA also covers business associates (BAs) and other vendors. Because BAs (or vendors) are contracted with CEs to provide services and activities that may allow them access to PHI, they are bound by the same requirements to safeguard and protect patient health information. In these situations, if a CE has a business associate agreement (BAA) with a BA or a vendor, they are allowed to disclose patient health information for the purpose of Treatment, Payment, and Healthcare Operations (TPO).
Disclosing PHI
There are several different situations where a CE may disclose PHI under HIPAA. They include incidental uses and disclosures, disclosures between CEs, and communicating with patients. While a CE is allowed to disclose PHI in each of these situations, there are guidelines and requirements in each situation to comply with HIPAA standards.
Incidental uses and disclosures are "a secondary disclosure that cannot be reasonably prevented, is limited in nature, and that occurs as a result of another use or disclosure that is permitted by the Rule" (HHS.gov).
Examples of incidental uses and disclosures:
- Sign-in Sheets - Sign-in sheets are permitted under HIPAA as long as they appropriately limit the amount of information required to the minimum necessary. They can only include the doctor's name, the patient's name, the appointment time, and the patient's time of arrival for the appointment. For example, a sign-in sheet doesn't need to have the reason for the visit listed, but the patient's name and doctor's name would be allowed.
- Patient Check-in - HIPAA permits oral disclosures while checking in a patient in the same way that it permits disclosures on a sign-in sheet. However, the information disclosed must be appropriately limited. For example, when checking in a patient, you may ask their name and what doctor they are there to see. While doing so, it is important to speak quietly and be aware of those around you.
- Confidential Conversations with Other Providers or Patients - To ensure reasonable safeguards for patient health information, providers need to be mindful of their surroundings when discussing PHI. For example, if a provider needs to review patient history with a nurse, it should be done in a private office or by speaking quietly if a private location is not available. Providers should not mention patient names, if possible. Another way to safeguard patient information is by talking quietly while discussing a patient's condition with family in a waiting room.
Disclosures between CEs, such as a provider disclosing patient treatment information to another physician or hospital for additional treatment, is permissible. For this type of disclosure, the minimum necessary standards do not apply; however, the provider may choose to disclose the minimum necessary information for any disclosures to which the standard applies. Additionally, CEs are permitted to communicate with patients about their care including information that is classified as PHI. Patients can also give consent for CEs to release PHI to family members or friends, or other individuals involved in their care or the payment of their care.

Communication between CEs and other providers or CEs and patients can be made in several ways as long as reasonable safeguards are applied. Everyday methods of communication include mail, facsimile (fax), email, or phone. Let's review some common reasonable safeguards for each mode of communication:
- Mail (such as the US Postal Service) - It is important to consider the confidentiality and security of the information being sent by mail. Using envelopes with security lining, marking the envelopes as "confidential," and verifying the envelope is addressed to the correct organization or individual are all essential ways to safeguard PHI when mailing the information.
- Facsimile (fax) - When using a traditional fax machine, a CE can apply the same considerations regarding the confidentiality and security of the transmitted information. Keeping the fax machine in a secure location where only those authorized can use it, using cover sheets with an appropriate privacy disclaimer, verifying the correct fax number before sending a fax, and logging faxes to track them are all examples of reasonable safeguards when sharing PHI by fax.
- Email - While encrypted email is the safest and most preferred method of safeguarding email communication, it is not always required. Other safeguards can include limiting the information contained in an email to the minimum necessary, avoiding transmitting highly sensitive PHI, verifying the recipient's email address, and always including a privacy statement.
- Phone - Making phone calls in a private location is always preferred. However, if that is not possible, lowering your voice in the presence of others and discussing minimum necessary information are appropriate safeguards for protecting PHI while on a phone call. Verifying the phone number before calling and requiring individuals to authenticate themselves by providing their name, address, and/or date of birth when answering the phone are additional recommended safeguards when calling patients to discuss their personal health information.
So, what's the general consensus when it comes to PHI?
As mentioned previously, PHI, including ePHI, refers to individually identifiable information relating to the health status of an individual. Protecting patient privacy including information that could reveal the identity of an individual, their medical history, or their payment history is obviously very important when it comes to patient care. The general idea may seem very simple; treat patient health information as you would like yours treated, and don't tell those who do not need to know. However, it requires creating policies and procedures, providing and taking training, and conducting regular risk analyses. It also requires understanding when to disclose PHI, to whom, and how to do so safely.
Protecting and safeguarding patient health information is an ongoing process and HCP is here to help. We offer training and support to make sure everyone in your organization knows how to safeguard PHI. In the event a breach was to happen, our expanded HIPAA program has you covered. With access to our online breach log, you can submit your "suspected" breaches to us for determination and mitigation. We will determine if a breach has occurred, who needs to be notified, and what corrective action needs to be taken. HCP will also provide you with all the necessary information required by the Department of Health and Human Services.

